Single sign-on (SSO)
To avoid repetitive logins, Single sign-on (SSO) is used to allow a user to log in with a single ID and password to many related systems without having to re-enter authentication credentials. SSO is also useful when logging directly into a system. SSO solutions limit repetitive requests for credentials when users access a variety of systems or applications, saving time and making the authentication experience easier for end-users.
By default, your system includes a basic authentication service named Platform Authentication, which uses the default servlet PRAuth. You can save this service with a new name and change it, and you can create any type of authentication service, including the basic type. The default servlet provides a unified authentication gateway so that you do not need to edit any external files or restart the server for new authentication services.
To override or extend the default authentication process, create and configure an authentication service.
In the center of the following image, slide the vertical line to compare the login experience with and without SSO.
SSO configuration
You can configure your application to authenticate users by using single sign-on (SSO) and external identity providers with one of the following authentication methods. To learn how to configure each authentication model with Pega Platform™, see the following help topics.
You can set up an SSO solution by configuring provider configuration, including endpoints for authorization, token, user info, and logout. If you prefer to use a well-known configuration of your service provider, you can import this metadata from a URL or a file.
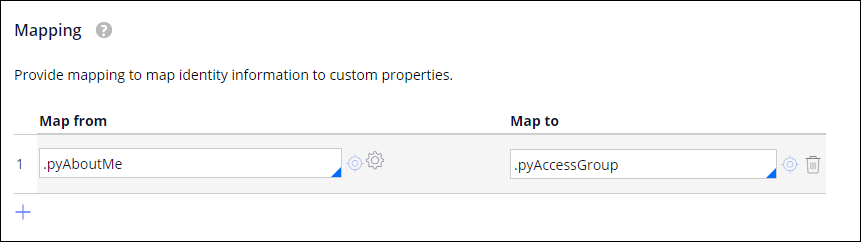
Property mapping
You can use the property mappings to take information obtained from the identity provider and map that information to the data model for an operator ID. For example, workgroups, access groups, and time zones can all be mapped from information obtained from the identity provider. In the following example, the properties contained in .pyAboutMe map to .pyAccessGroup:
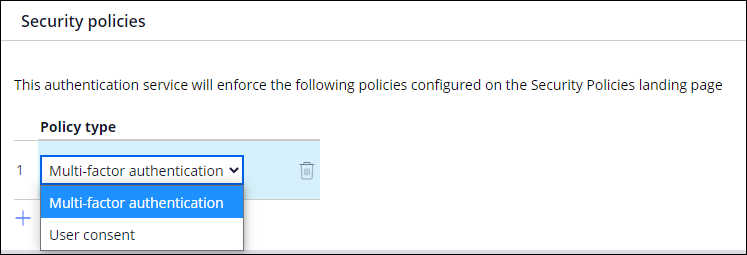
Security policies on authentication services
You can configure the required security enforcement policies for your authentication service. On the Edit Authentication Service page, click the Security policies tab, and then select the appropriate policy from the Policy type drop-down list.
For each policy type, there are different configuration requirements:
- If you select Multi-factor authentication, you must map properties such as email address or phone number from the email or SMS receiver account by using the Mapping tab.
- If you select User consent, the section pyPostAuthConsentScreen displays to the user after authentication. You can customize this section.
Check your knowledge with the following interaction.
If you are having problems with your training, please review the Pega Academy Support FAQs.
Want to help us improve this content?