Pega Web Mashup authentication
Pega Web Mashup enables you to embed a Pega application in another web application. The system must authenticate the user before displaying the application mashup on the external web page. Similar to an SSO configuration, a third-party authentication module manages the authentication of Pega Web Mashup users.
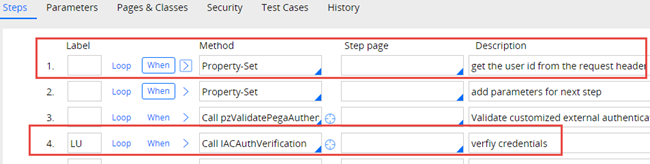
Pega provides a standard authentication service named Internet Application Composer (IAC) Authentication for Pega Web Mashup configurations. The standard web.xml contains a servlet named IAC that references this authentication service instance. The instance references standard IAC authentication activities by default. Unlike other custom authentication services, you do not need to create an IAC authentication service and add a reference to it in web.xml. The following image shows the servlet and authentication service.
The standard IAC authentication service is designed for quick Pega Web Mashup implementation in a design environment. However, you need to update the authentication activities to ensure adequate security in a production environment.
The standard IACAuthentication activity extracts values from custom HTTP headers in the HTTP request to identify an authenticated operator. The activity uses the operator's identifier to verify that the user is in the system. The third-party authentication module typically provides this operator information. Step 4 of the activity is configured to have the IACAuthVerification activity return the token to the authentication module and verify the module generated the token.
Caution: Remove the IAC servlet from the web.xml file if you are not using Pega Mashup.
Pega Cloud customers do not have access to modify web.xml files. Contact Pega Cloud services to implement the necessary changes.
Pega Cloud customers do not have access to modify web.xml files. Contact Pega Cloud services to implement the necessary changes.
Check your knowledge with the following interaction:
User authentication
When users log in to the mashup application, the IACAuthentication activity uses information in the HTTP request header to identify a corresponding Pega Platform™ operator ID record.
If an operator ID record for the user does not exist, the activity creates a record for the user. The activity customizes a template Operator ID or model operator using information in the HTTP request header to create an operator ID record for the user.
For example, consider a banking application with a Pega Web Mashup. The bank database includes login credentials for its customers, but the Pega application does not have login credentials for new application users. When a new user logs in, the system creates a guest ID, which is an operator ID based on a model user template containing relevant user attributes. This process enables new users to start working in their applications immediately. Users do not have to wait for their operator records to be manually created in Pega.
The IACAuthentication activity requires that the HTTP request provides the following information to create an Operator ID.
- pyuseridentifier – Operator's identifier
- pyusername – Operator's full name
- pyorganization – Operator’s organization name
- pyorgdivision – Operator’s division name
- pyorgunit – Operator’s organization unit name
The organization, division, and org unit information in the header is used to identify the appropriate org unit record in Pega Platform. The model operator associated with that org unit is the template for creating an operator ID record for the new user. The identifier and full name are used to customize the operator ID for the user.
Caution: When generating operator ID records for web mashup users, set the IACAuthentication service to use externally stored credentials, rather than credentials stored in Pega Platform.
Web mashup Broken Access Control
Broken Access control (BAC) refers to all access control issues in web applications that allow end users to gain unauthorized access to privileged data and functionality. Users can bypass access control checks by leveraging vulnerabilities such as URL-based requests that do not verify user privileges. To protect your application, Pega Web Mashup requests are strictly validated against the mashup channel configurations.
Note: Before Pega Platform version 8.5, unregistered and unencrypted requests from the client were not blocked by default, and mashups were secured as a part of BAC mitigation support. As of Pega Platform version 8.5, existing mashups without the channel ID parameter do not load and users see an access control warning. Updates to Pega Platform 8.5 require that you create a new mashup and generate a new mashup code for redeployment.
Check your knowledge with the following interaction:
This Topic is available in the following Module:
If you are having problems with your training, please review the Pega Academy Support FAQs.
Want to help us improve this content?