Application access
The role-based access control model
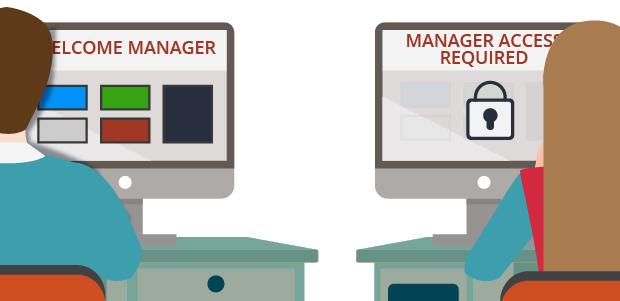
Application and data security are major concerns due to risks of customer loss, data breaches, and legal and financial penalties. You can satisfy common security requirements by controlling the application features and functions users can access using role-based access control (RBAC). With RBAC, you configure access by defining roles with the desired authorization and privileges. For example, only managers can access the case manager portal, which displays the work of all members of the team.
Note: Configuring appropriate access control is only one aspect of securing an application. For a complete list of security leading practices, consult the Security Checklist awareness module and the Security Checklist for Pega Platform deployment.
Access control depends on two factors: authentication and authorization. Authentication confirms the identity of a user and verifies that the user is allowed access to an application. In Pega Platform™, the record for the operator ID allows for authentication of a user. Authorization determines what data the user can view and what actions the user can perform. In Pega Platform, the records for the access group and application allow for authorization of a user.
In the following image, click the + icons to learn more about the records that facilitate authentication.
Access groups and access roles
You can create multiple access groups that reference the same application to achieve different levels of access control.
Note: Access groups in Dev Studio align with the role that developers can assign to users in App Studio.
An access role in Dev Studio categorizes users according to their job function. Each access group identifies one or more access roles. Each access role represents how a set of users interacts with an application to create and process cases. Access roles are associated with a set of permissions. For example, in an application for managing purchase requests, any user can submit a time off request, but only an administrator can delete time-off requests.
When an access group lists more than one role, Pega Platform applies the most permissive setting across all the listed roles.
In the center of the following image, drag the vertical line to view the differences between an example administrator access group and user access group record.
If you are having problems with your training, please review the Pega Academy Support FAQs.
Want to help us improve this content?
